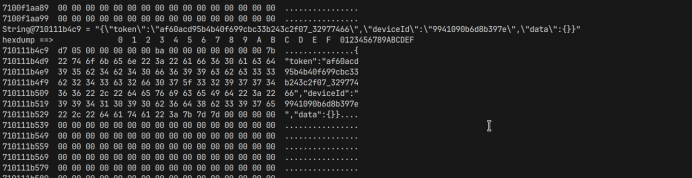
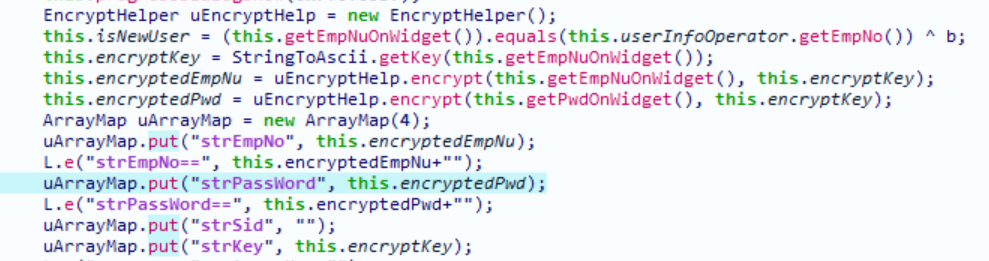
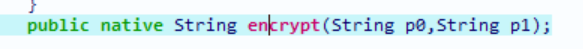
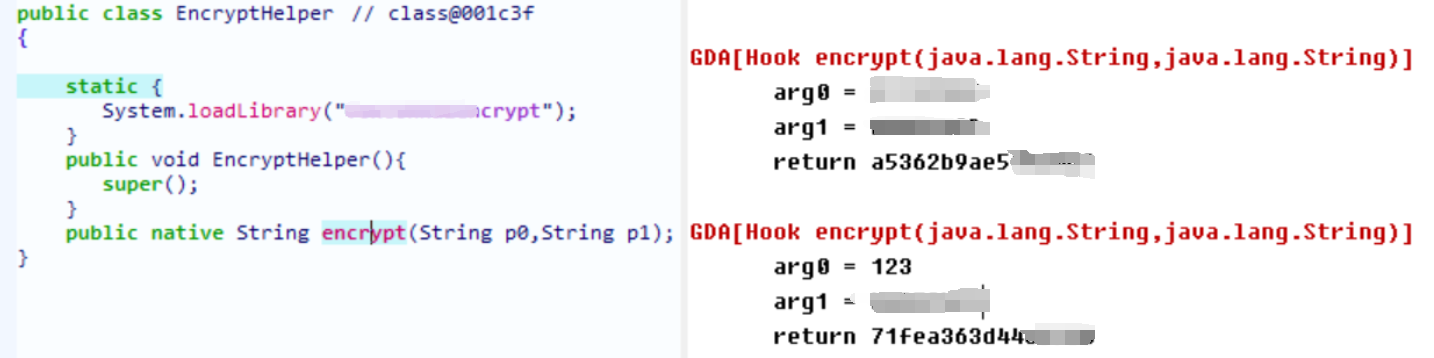
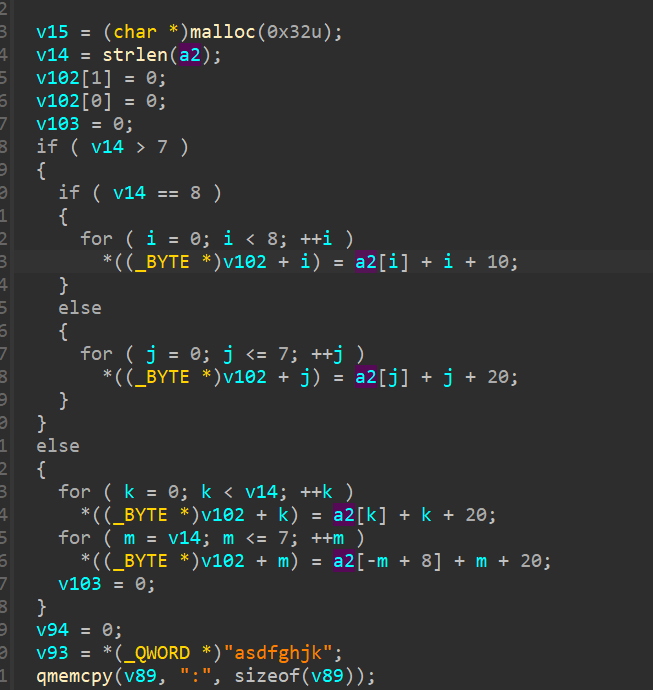
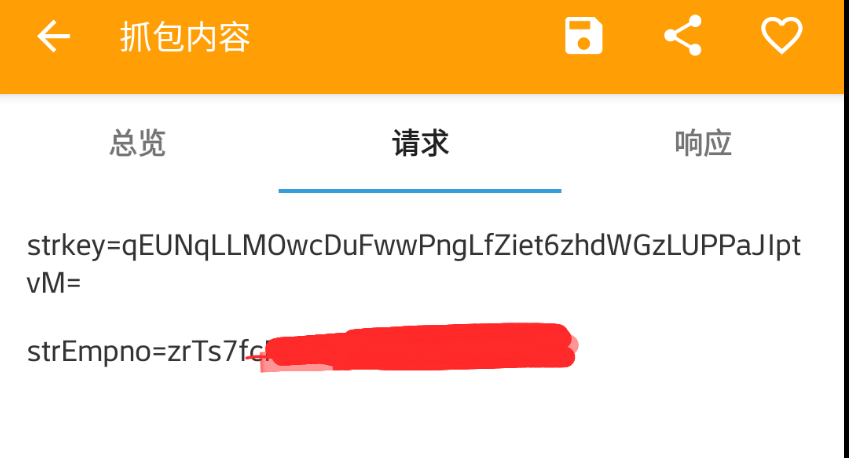
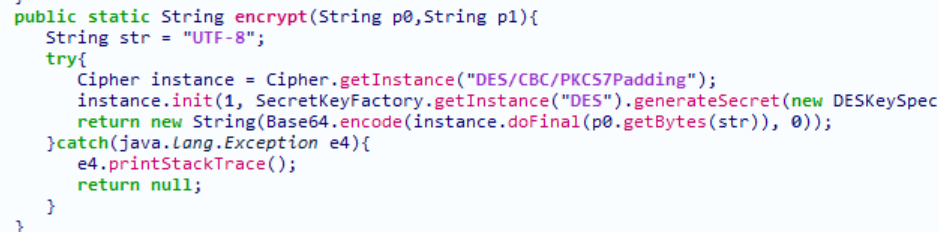
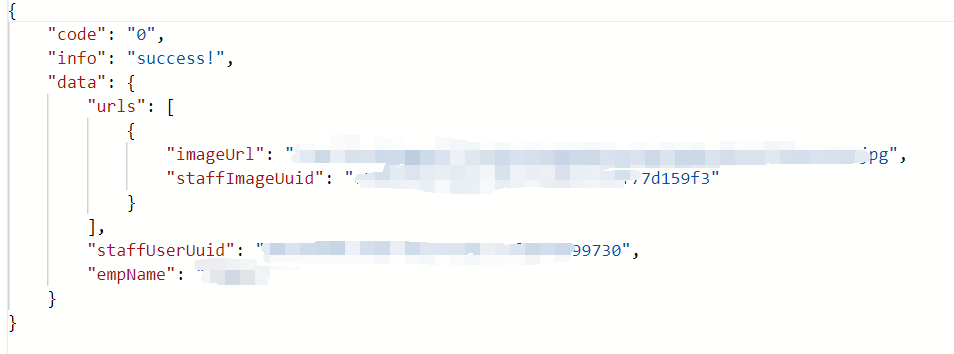
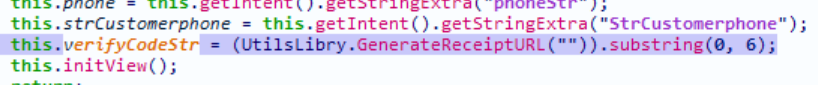
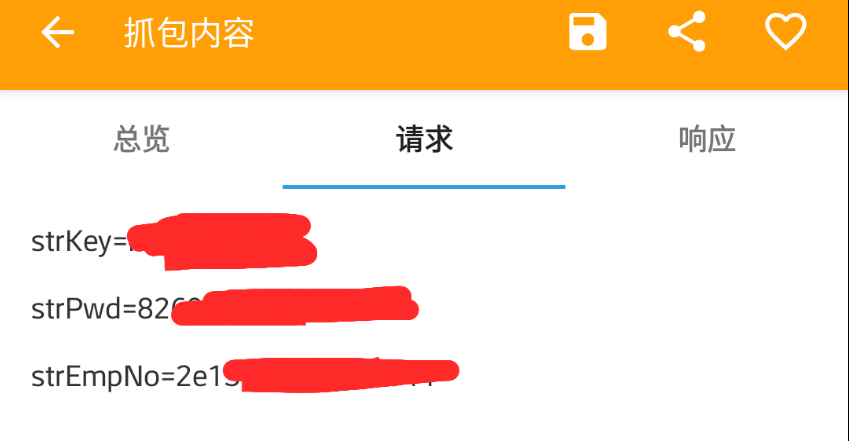
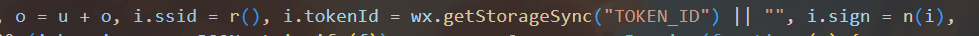
function getsign() {
var i, g = arguments;
i = { 'phoneNumber': '17628818007', 'ssid': '', 'tokenId': '' }
return i.ssid = getTime(), i.tokenId = false || "", i.sign = sign(i)
}
function r(r) {
var a = new Array(), n = r.length, s = parseInt(n / 4), f = n % 4, o = 0;
for (o = 0; o < s; o++) a[o] = e(r.substring(4 * o + 0, 4 * o + 4));
return f > 0 && (a[o] = e(r.substring(4 * o + 0, n))), a;
}
function e(r) {
var e = r.length, a = new Array(64), n = 0, s = 0, f = 0, o = 0;
if (e < 4) {
for (n = 0; n < e; n++) {
var c = r.charCodeAt(n);
for (s = 0; s < 16; s++) {
var t = 1, l = 0;
for (l = 15; l > s; l--) t *= 2;
a[16 * n + s] = parseInt(c / t) % 2;
}
}
for (f = e; f < 4; f++) {
c = 0;
for (o = 0; o < 16; o++) {
t = 1, l = 0;
for (l = 15; l > o; l--) t *= 2;
a[16 * f + o] = parseInt(c / t) % 2;
}
}
} else for (n = 0; n < 4; n++) {
c = r.charCodeAt(n);
for (s = 0; s < 16; s++) {
t = 1;
for (l = 15; l > s; l--) t *= 2;
a[16 * n + s] = parseInt(c / t) % 2;
}
}
return a;
}
function a(r) {
var e;
switch (r) {
case "0000":
e = "0";
break;
case "0001":
e = "1";
break;
case "0010":
e = "2";
break;
case "0011":
e = "3";
break;
case "0100":
e = "4";
break;
case "0101":
e = "5";
break;
case "0110":
e = "6";
break;
case "0111":
e = "7";
break;
case "1000":
e = "8";
break;
case "1001":
e = "9";
break;
case "1010":
e = "A";
break;
case "1011":
e = "B";
break;
case "1100":
e = "C";
break;
case "1101":
e = "D";
break;
case "1110":
e = "E";
break;
case "1111":
e = "F";
}
return e;
}
function n(r) {
for (var e = "", n = 0; n < 16; n++) {
for (var s = "", f = 0; f < 4; f++) s += r[4 * n + f];
e += a(s);
}
return e;
}
function s(r, e) {
var a = k(e), n = f(r), s = new Array(32), b = new Array(32), i = new Array(32), w = 0, v = 0, A = 0, y = 0, h = 0;
for (A = 0; A < 32; A++) s[A] = n[A], b[A] = n[32 + A];
for (w = 0; w < 16; w++) {
for (v = 0; v < 32; v++) i[v] = s[v], s[v] = b[v];
var g = new Array(48);
for (y = 0; y < 48; y++) g[y] = a[w][y];
var p = c(l(t(c(o(b), g))), i);
for (h = 0; h < 32; h++) b[h] = p[h];
}
var I = new Array(64);
for (w = 0; w < 32; w++) I[w] = b[w], I[32 + w] = s[w];
return u(I);
}
function f(r) {
for (var e = new Array(64), a = 0, n = 1, s = 0; a < 4; a++, n += 2, s += 2) for (var f = 7, o = 0; f >= 0; f--,
o++) e[8 * a + o] = r[8 * f + n], e[8 * a + o + 32] = r[8 * f + s];
return e;
}
function o(r) {
for (var e = new Array(48), a = 0; a < 8; a++) e[6 * a + 0] = 0 == a ? r[31] : r[4 * a - 1],
e[6 * a + 1] = r[4 * a + 0], e[6 * a + 2] = r[4 * a + 1], e[6 * a + 3] = r[4 * a + 2],
e[6 * a + 4] = r[4 * a + 3], e[6 * a + 5] = 7 == a ? r[0] : r[4 * a + 4];
return e;
}
function c(r, e) {
for (var a = new Array(r.length), n = 0; n < r.length; n++) a[n] = r[n] ^ e[n];
return a;
}
function t(r) {
for (var e = new Array(32), a = "", n = [[14, 4, 13, 1, 2, 15, 11, 8, 3, 10, 6, 12, 5, 9, 0, 7], [0, 15, 7, 4, 14, 2, 13, 1, 10, 6, 12, 11, 9, 5, 3, 8], [4, 1, 14, 8, 13, 6, 2, 11, 15, 12, 9, 7, 3, 10, 5, 0], [15, 12, 8, 2, 4, 9, 1, 7, 5, 11, 3, 14, 10, 0, 6, 13]], s = [[15, 1, 8, 14, 6, 11, 3, 4, 9, 7, 2, 13, 12, 0, 5, 10], [3, 13, 4, 7, 15, 2, 8, 14, 12, 0, 1, 10, 6, 9, 11, 5], [0, 14, 7, 11, 10, 4, 13, 1, 5, 8, 12, 6, 9, 3, 2, 15], [13, 8, 10, 1, 3, 15, 4, 2, 11, 6, 7, 12, 0, 5, 14, 9]], f = [[10, 0, 9, 14, 6, 3, 15, 5, 1, 13, 12, 7, 11, 4, 2, 8], [13, 7, 0, 9, 3, 4, 6, 10, 2, 8, 5, 14, 12, 11, 15, 1], [13, 6, 4, 9, 8, 15, 3, 0, 11, 1, 2, 12, 5, 10, 14, 7], [1, 10, 13, 0, 6, 9, 8, 7, 4, 15, 14, 3, 11, 5, 2, 12]], o = [[7, 13, 14, 3, 0, 6, 9, 10, 1, 2, 8, 5, 11, 12, 4, 15], [13, 8, 11, 5, 6, 15, 0, 3, 4, 7, 2, 12, 1, 10, 14, 9], [10, 6, 9, 0, 12, 11, 7, 13, 15, 1, 3, 14, 5, 2, 8, 4], [3, 15, 0, 6, 10, 1, 13, 8, 9, 4, 5, 11, 12, 7, 2, 14]], c = [[2, 12, 4, 1, 7, 10, 11, 6, 8, 5, 3, 15, 13, 0, 14, 9], [14, 11, 2, 12, 4, 7, 13, 1, 5, 0, 15, 10, 3, 9, 8, 6], [4, 2, 1, 11, 10, 13, 7, 8, 15, 9, 12, 5, 6, 3, 0, 14], [11, 8, 12, 7, 1, 14, 2, 13, 6, 15, 0, 9, 10, 4, 5, 3]], t = [[12, 1, 10, 15, 9, 2, 6, 8, 0, 13, 3, 4, 14, 7, 5, 11], [10, 15, 4, 2, 7, 12, 9, 5, 6, 1, 13, 14, 0, 11, 3, 8], [9, 14, 15, 5, 2, 8, 12, 3, 7, 0, 4, 10, 1, 13, 11, 6], [4, 3, 2, 12, 9, 5, 15, 10, 11, 14, 1, 7, 6, 0, 8, 13]], l = [[4, 11, 2, 14, 15, 0, 8, 13, 3, 12, 9, 7, 5, 10, 6, 1], [13, 0, 11, 7, 4, 9, 1, 10, 14, 3, 5, 12, 2, 15, 8, 6], [1, 4, 11, 13, 12, 3, 7, 14, 10, 15, 6, 8, 0, 5, 9, 2], [6, 11, 13, 8, 1, 4, 10, 7, 9, 5, 0, 15, 14, 2, 3, 12]], u = [[13, 2, 8, 4, 6, 15, 11, 1, 10, 9, 3, 14, 5, 0, 12, 7], [1, 15, 13, 8, 10, 3, 7, 4, 12, 5, 6, 11, 0, 14, 9, 2], [7, 11, 4, 1, 9, 12, 14, 2, 0, 6, 10, 13, 15, 3, 5, 8], [2, 1, 14, 7, 4, 10, 8, 13, 15, 12, 9, 0, 3, 5, 6, 11]], k = 0; k < 8; k++) {
var i, w;
switch (i = 2 * r[6 * k + 0] + r[6 * k + 5], w = 2 * r[6 * k + 1] * 2 * 2 + 2 * r[6 * k + 2] * 2 + 2 * r[6 * k + 3] + r[6 * k + 4],
k) {
case 0:
a = b(n[i][w]);
break;
case 1:
a = b(s[i][w]);
break;
case 2:
a = b(f[i][w]);
break;
case 3:
a = b(o[i][w]);
break;
case 4:
a = b(c[i][w]);
break;
case 5:
a = b(t[i][w]);
break;
case 6:
a = b(l[i][w]);
break;
case 7:
a = b(u[i][w]);
}
e[4 * k + 0] = parseInt(a.substring(0, 1)), e[4 * k + 1] = parseInt(a.substring(1, 2)),
e[4 * k + 2] = parseInt(a.substring(2, 3)), e[4 * k + 3] = parseInt(a.substring(3, 4));
}
return e;
}
function l(r) {
var e = new Array(32);
return e[0] = r[15], e[1] = r[6], e[2] = r[19], e[3] = r[20], e[4] = r[28], e[5] = r[11],
e[6] = r[27], e[7] = r[16], e[8] = r[0], e[9] = r[14], e[10] = r[22], e[11] = r[25],
e[12] = r[4], e[13] = r[17], e[14] = r[30], e[15] = r[9], e[16] = r[1], e[17] = r[7],
e[18] = r[23], e[19] = r[13], e[20] = r[31], e[21] = r[26], e[22] = r[2], e[23] = r[8],
e[24] = r[18], e[25] = r[12], e[26] = r[29], e[27] = r[5], e[28] = r[21], e[29] = r[10],
e[30] = r[3], e[31] = r[24], e;
}
function u(r) {
var e = new Array(64);
return e[0] = r[39], e[1] = r[7], e[2] = r[47], e[3] = r[15], e[4] = r[55], e[5] = r[23],
e[6] = r[63], e[7] = r[31], e[8] = r[38], e[9] = r[6], e[10] = r[46], e[11] = r[14],
e[12] = r[54], e[13] = r[22], e[14] = r[62], e[15] = r[30], e[16] = r[37], e[17] = r[5],
e[18] = r[45], e[19] = r[13], e[20] = r[53], e[21] = r[21], e[22] = r[61], e[23] = r[29],
e[24] = r[36], e[25] = r[4], e[26] = r[44], e[27] = r[12], e[28] = r[52], e[29] = r[20],
e[30] = r[60], e[31] = r[28], e[32] = r[35], e[33] = r[3], e[34] = r[43], e[35] = r[11],
e[36] = r[51], e[37] = r[19], e[38] = r[59], e[39] = r[27], e[40] = r[34], e[41] = r[2],
e[42] = r[42], e[43] = r[10], e[44] = r[50], e[45] = r[18], e[46] = r[58], e[47] = r[26],
e[48] = r[33], e[49] = r[1], e[50] = r[41], e[51] = r[9], e[52] = r[49], e[53] = r[17],
e[54] = r[57], e[55] = r[25], e[56] = r[32], e[57] = r[0], e[58] = r[40], e[59] = r[8],
e[60] = r[48], e[61] = r[16], e[62] = r[56], e[63] = r[24], e;
}
function b(r) {
var e = "";
switch (r) {
case 0:
e = "0000";
break;
case 1:
e = "0001";
break;
case 2:
e = "0010";
break;
case 3:
e = "0011";
break;
case 4:
e = "0100";
break;
case 5:
e = "0101";
break;
case 6:
e = "0110";
break;
case 7:
e = "0111";
break;
case 8:
e = "1000";
break;
case 9:
e = "1001";
break;
case 10:
e = "1010";
break;
case 11:
e = "1011";
break;
case 12:
e = "1100";
break;
case 13:
e = "1101";
break;
case 14:
e = "1110";
break;
case 15:
e = "1111";
}
return e;
}
function k(r) {
var e = new Array(56), a = new Array();
a[0] = new Array(), a[1] = new Array(), a[2] = new Array(), a[3] = new Array(),
a[4] = new Array(), a[5] = new Array(), a[6] = new Array(), a[7] = new Array(),
a[8] = new Array(), a[9] = new Array(), a[10] = new Array(), a[11] = new Array(),
a[12] = new Array(), a[13] = new Array(), a[14] = new Array(), a[15] = new Array();
for (var n = [1, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 1], s = 0; s < 7; s++) for (var f = 0, o = 7; f < 8; f++,
o--) e[8 * s + f] = r[8 * o + s];
s = 0;
for (s = 0; s < 16; s++) {
var c = 0, t = 0;
for (f = 0; f < n[s]; f++) {
for (c = e[0], t = e[28], o = 0; o < 27; o++) e[o] = e[o + 1], e[28 + o] = e[29 + o];
e[27] = c, e[55] = t;
}
var l = new Array(48);
switch (l[0] = e[13], l[1] = e[16], l[2] = e[10], l[3] = e[23], l[4] = e[0], l[5] = e[4],
l[6] = e[2], l[7] = e[27], l[8] = e[14], l[9] = e[5], l[10] = e[20], l[11] = e[9],
l[12] = e[22], l[13] = e[18], l[14] = e[11], l[15] = e[3], l[16] = e[25], l[17] = e[7],
l[18] = e[15], l[19] = e[6], l[20] = e[26], l[21] = e[19], l[22] = e[12], l[23] = e[1],
l[24] = e[40], l[25] = e[51], l[26] = e[30], l[27] = e[36], l[28] = e[46], l[29] = e[54],
l[30] = e[29], l[31] = e[39], l[32] = e[50], l[33] = e[44], l[34] = e[32], l[35] = e[47],
l[36] = e[43], l[37] = e[48], l[38] = e[38], l[39] = e[55], l[40] = e[33], l[41] = e[52],
l[42] = e[45], l[43] = e[41], l[44] = e[49], l[45] = e[35], l[46] = e[28], l[47] = e[31],
s) {
case 0:
for (var u = 0; u < 48; u++) a[0][u] = l[u];
break;
case 1:
for (u = 0; u < 48; u++) a[1][u] = l[u];
break;
case 2:
for (u = 0; u < 48; u++) a[2][u] = l[u];
break;
case 3:
for (u = 0; u < 48; u++) a[3][u] = l[u];
break;
case 4:
for (u = 0; u < 48; u++) a[4][u] = l[u];
break;
case 5:
for (u = 0; u < 48; u++) a[5][u] = l[u];
break;
case 6:
for (u = 0; u < 48; u++) a[6][u] = l[u];
break;
case 7:
for (u = 0; u < 48; u++) a[7][u] = l[u];
break;
case 8:
for (u = 0; u < 48; u++) a[8][u] = l[u];
break;
case 9:
for (u = 0; u < 48; u++) a[9][u] = l[u];
break;
case 10:
for (u = 0; u < 48; u++) a[10][u] = l[u];
break;
case 11:
for (u = 0; u < 48; u++) a[11][u] = l[u];
break;
case 12:
for (u = 0; u < 48; u++) a[12][u] = l[u];
break;
case 13:
for (u = 0; u < 48; u++) a[13][u] = l[u];
break;
case 14:
for (u = 0; u < 48; u++) a[14][u] = l[u];
break;
case 15:
for (u = 0; u < 48; u++) a[15][u] = l[u];
}
}
return a;
}
// module.exports = {
function getTime() {
return function (a, f, o, c) {
var t, l, u, b, k, i, w = a.length, v = "";
null != f && "" != f && (t = r(f), b = t.length);
null != o && "" != o && (l = r(o), k = l.length);
null != c && "" != c && (u = r(c), i = u.length);
if (w > 0) if (w < 4) {
var A = e(a);
if (null != f && "" != f && null != o && "" != o && null != c && "" != c) {
for ($ = A, y = 0; y < b; y++) $ = s($, t[y]);
for (C = 0; C < k; C++) $ = s($, l[C]);
for (d = 0; d < i; d++) $ = s($, u[d]);
x = $;
} else if (null != f && "" != f && null != o && "" != o) {
for ($ = A, y = 0; y < b; y++) $ = s($, t[y]);
for (C = 0; C < k; C++) $ = s($, l[C]);
x = $;
} else if (null != f && "" != f) {
var y = 0;
for ($ = A, y = 0; y < b; y++) $ = s($, t[y]);
x = $;
}
v = n(x);
} else {
var h = parseInt(w / 4), g = w % 4, p = 0;
for (p = 0; p < h; p++) {
var I = e(a.substring(4 * p + 0, 4 * p + 4));
if (null != f && "" != f && null != o && "" != o && null != c && "" != c) {
for ($ = I, y = 0; y < b; y++) $ = s($, t[y]);
for (C = 0; C < k; C++) $ = s($, l[C]);
for (d = 0; d < i; d++) $ = s($, u[d]);
x = $;
} else if (null != f && "" != f && null != o && "" != o) {
for ($ = I, y = 0; y < b; y++) $ = s($, t[y]);
for (C = 0; C < k; C++) $ = s($, l[C]);
x = $;
} else if (null != f && "" != f) {
for ($ = I, y = 0; y < b; y++) $ = s($, t[y]);
x = $;
}
v += n(x);
}
if (g > 0) {
var x;
I = e(a.substring(4 * h + 0, w));
if (null != f && "" != f && null != o && "" != o && null != c && "" != c) {
var d;
for ($ = I, y = 0; y < b; y++) $ = s($, t[y]);
for (C = 0; C < k; C++) $ = s($, l[C]);
for (d = 0; d < i; d++) $ = s($, u[d]);
x = $;
} else if (null != f && "" != f && null != o && "" != o) {
var C;
for ($ = I, y = 0; y < b; y++) $ = s($, t[y]);
for (C = 0; C < k; C++) $ = s($, l[C]);
x = $;
} else if (null != f && "" != f) {
var $;
for ($ = I, y = 0; y < b; y++) $ = s($, t[y]);
x = $;
}
v += n(x);
}
}
return v;
}("saywash#" + new Date().valueOf(), "hlF#$1x)", "hlG#$2x)", "hlH#$3x)");
}
function sign(e) {
Array.prototype.indexVf = function (r) {
for (var e = 0; e < this.length; e++) if (this[e] == r) return e;
}
var t = [], n = [], i = [];
for (var s in e) t.push(s), i.push(s), n.push(e[s]);
for (var o = i.sort(), u = "SING=HLYF", f = 0; f < o.length; f++) if ("tokenId" != o[f] && "ssid" != o[f] && "sign" != o[f]) {
var a = t.indexVf(o[f]);
"" != n[a] && null != n[a] && (u = u + "&" + o[f] + "=" + n[a]);
}
return "SING=HLYF" == (u = u.toUpperCase()) && (u = "SING=HLYF&"), u = md5(u);
}
function md5(string) {
function md5_RotateLeft(lValue, iShiftBits) {
return (lValue << iShiftBits) | (lValue >>> (32 - iShiftBits));
}
function md5_AddUnsigned(lX, lY) {
var lX4, lY4, lX8, lY8, lResult;
lX8 = (lX & 0x80000000);
lY8 = (lY & 0x80000000);
lX4 = (lX & 0x40000000);
lY4 = (lY & 0x40000000);
lResult = (lX & 0x3FFFFFFF) + (lY & 0x3FFFFFFF);
if (lX4 & lY4) {
return (lResult ^ 0x80000000 ^ lX8 ^ lY8);
}
if (lX4 | lY4) {
if (lResult & 0x40000000) {
return (lResult ^ 0xC0000000 ^ lX8 ^ lY8);
} else {
return (lResult ^ 0x40000000 ^ lX8 ^ lY8);
}
} else {
return (lResult ^ lX8 ^ lY8);
}
}
function md5_F(x, y, z) {
return (x & y) | ((~x) & z);
}
function md5_G(x, y, z) {
return (x & z) | (y & (~z));
}
function md5_H(x, y, z) {
return (x ^ y ^ z);
}
function md5_I(x, y, z) {
return (y ^ (x | (~z)));
}
function md5_FF(a, b, c, d, x, s, ac) {
a = md5_AddUnsigned(a, md5_AddUnsigned(md5_AddUnsigned(md5_F(b, c, d), x), ac));
return md5_AddUnsigned(md5_RotateLeft(a, s), b);
};
function md5_GG(a, b, c, d, x, s, ac) {
a = md5_AddUnsigned(a, md5_AddUnsigned(md5_AddUnsigned(md5_G(b, c, d), x), ac));
return md5_AddUnsigned(md5_RotateLeft(a, s), b);
};
function md5_HH(a, b, c, d, x, s, ac) {
a = md5_AddUnsigned(a, md5_AddUnsigned(md5_AddUnsigned(md5_H(b, c, d), x), ac));
return md5_AddUnsigned(md5_RotateLeft(a, s), b);
};
function md5_II(a, b, c, d, x, s, ac) {
a = md5_AddUnsigned(a, md5_AddUnsigned(md5_AddUnsigned(md5_I(b, c, d), x), ac));
return md5_AddUnsigned(md5_RotateLeft(a, s), b);
};
function md5_ConvertToWordArray(string) {
var lWordCount;
var lMessageLength = string.length;
var lNumberOfWords_temp1 = lMessageLength + 8;
var lNumberOfWords_temp2 = (lNumberOfWords_temp1 - (lNumberOfWords_temp1 % 64)) / 64;
var lNumberOfWords = (lNumberOfWords_temp2 + 1) * 16;
var lWordArray = Array(lNumberOfWords - 1);
var lBytePosition = 0;
var lByteCount = 0;
while (lByteCount < lMessageLength) {
lWordCount = (lByteCount - (lByteCount % 4)) / 4;
lBytePosition = (lByteCount % 4) * 8;
lWordArray[lWordCount] = (lWordArray[lWordCount] | (string.charCodeAt(lByteCount) << lBytePosition));
lByteCount++;
}
lWordCount = (lByteCount - (lByteCount % 4)) / 4;
lBytePosition = (lByteCount % 4) * 8;
lWordArray[lWordCount] = lWordArray[lWordCount] | (0x80 << lBytePosition);
lWordArray[lNumberOfWords - 2] = lMessageLength << 3;
lWordArray[lNumberOfWords - 1] = lMessageLength >>> 29;
return lWordArray;
};
function md5_WordToHex(lValue) {
var WordToHexValue = "", WordToHexValue_temp = "", lByte, lCount;
for (lCount = 0; lCount <= 3; lCount++) {
lByte = (lValue >>> (lCount * 8)) & 255;
WordToHexValue_temp = "0" + lByte.toString(16);
WordToHexValue = WordToHexValue + WordToHexValue_temp.substr(WordToHexValue_temp.length - 2, 2);
}
return WordToHexValue;
};
function md5_Utf8Encode(string) {
string = string.replace(/\r\n/g, "\n");
var utftext = "";
for (var n = 0; n < string.length; n++) {
var c = string.charCodeAt(n);
if (c < 128) {
utftext += String.fromCharCode(c);
} else if ((c > 127) && (c < 2048)) {
utftext += String.fromCharCode((c >> 6) | 192);
utftext += String.fromCharCode((c & 63) | 128);
} else {
utftext += String.fromCharCode((c >> 12) | 224);
utftext += String.fromCharCode(((c >> 6) & 63) | 128);
utftext += String.fromCharCode((c & 63) | 128);
}
}
return utftext;
};
var x = Array();
var k, AA, BB, CC, DD, a, b, c, d;
var S11 = 7, S12 = 12, S13 = 17, S14 = 22;
var S21 = 5, S22 = 9, S23 = 14, S24 = 20;
var S31 = 4, S32 = 11, S33 = 16, S34 = 23;
var S41 = 6, S42 = 10, S43 = 15, S44 = 21;
string = md5_Utf8Encode(string);
x = md5_ConvertToWordArray(string);
a = 0x67452301;
b = 0xEFCDAB89;
c = 0x98BADCFE;
d = 0x10325476;
for (k = 0; k < x.length; k += 16) {
AA = a;
BB = b;
CC = c;
DD = d;
a = md5_FF(a, b, c, d, x[k + 0], S11, 0xD76AA478);
d = md5_FF(d, a, b, c, x[k + 1], S12, 0xE8C7B756);
c = md5_FF(c, d, a, b, x[k + 2], S13, 0x242070DB);
b = md5_FF(b, c, d, a, x[k + 3], S14, 0xC1BDCEEE);
a = md5_FF(a, b, c, d, x[k + 4], S11, 0xF57C0FAF);
d = md5_FF(d, a, b, c, x[k + 5], S12, 0x4787C62A);
c = md5_FF(c, d, a, b, x[k + 6], S13, 0xA8304613);
b = md5_FF(b, c, d, a, x[k + 7], S14, 0xFD469501);
a = md5_FF(a, b, c, d, x[k + 8], S11, 0x698098D8);
d = md5_FF(d, a, b, c, x[k + 9], S12, 0x8B44F7AF);
c = md5_FF(c, d, a, b, x[k + 10], S13, 0xFFFF5BB1);
b = md5_FF(b, c, d, a, x[k + 11], S14, 0x895CD7BE);
a = md5_FF(a, b, c, d, x[k + 12], S11, 0x6B901122);
d = md5_FF(d, a, b, c, x[k + 13], S12, 0xFD987193);
c = md5_FF(c, d, a, b, x[k + 14], S13, 0xA679438E);
b = md5_FF(b, c, d, a, x[k + 15], S14, 0x49B40821);
a = md5_GG(a, b, c, d, x[k + 1], S21, 0xF61E2562);
d = md5_GG(d, a, b, c, x[k + 6], S22, 0xC040B340);
c = md5_GG(c, d, a, b, x[k + 11], S23, 0x265E5A51);
b = md5_GG(b, c, d, a, x[k + 0], S24, 0xE9B6C7AA);
a = md5_GG(a, b, c, d, x[k + 5], S21, 0xD62F105D);
d = md5_GG(d, a, b, c, x[k + 10], S22, 0x2441453);
c = md5_GG(c, d, a, b, x[k + 15], S23, 0xD8A1E681);
b = md5_GG(b, c, d, a, x[k + 4], S24, 0xE7D3FBC8);
a = md5_GG(a, b, c, d, x[k + 9], S21, 0x21E1CDE6);
d = md5_GG(d, a, b, c, x[k + 14], S22, 0xC33707D6);
c = md5_GG(c, d, a, b, x[k + 3], S23, 0xF4D50D87);
b = md5_GG(b, c, d, a, x[k + 8], S24, 0x455A14ED);
a = md5_GG(a, b, c, d, x[k + 13], S21, 0xA9E3E905);
d = md5_GG(d, a, b, c, x[k + 2], S22, 0xFCEFA3F8);
c = md5_GG(c, d, a, b, x[k + 7], S23, 0x676F02D9);
b = md5_GG(b, c, d, a, x[k + 12], S24, 0x8D2A4C8A);
a = md5_HH(a, b, c, d, x[k + 5], S31, 0xFFFA3942);
d = md5_HH(d, a, b, c, x[k + 8], S32, 0x8771F681);
c = md5_HH(c, d, a, b, x[k + 11], S33, 0x6D9D6122);
b = md5_HH(b, c, d, a, x[k + 14], S34, 0xFDE5380C);
a = md5_HH(a, b, c, d, x[k + 1], S31, 0xA4BEEA44);
d = md5_HH(d, a, b, c, x[k + 4], S32, 0x4BDECFA9);
c = md5_HH(c, d, a, b, x[k + 7], S33, 0xF6BB4B60);
b = md5_HH(b, c, d, a, x[k + 10], S34, 0xBEBFBC70);
a = md5_HH(a, b, c, d, x[k + 13], S31, 0x289B7EC6);
d = md5_HH(d, a, b, c, x[k + 0], S32, 0xEAA127FA);
c = md5_HH(c, d, a, b, x[k + 3], S33, 0xD4EF3085);
b = md5_HH(b, c, d, a, x[k + 6], S34, 0x4881D05);
a = md5_HH(a, b, c, d, x[k + 9], S31, 0xD9D4D039);
d = md5_HH(d, a, b, c, x[k + 12], S32, 0xE6DB99E5);
c = md5_HH(c, d, a, b, x[k + 15], S33, 0x1FA27CF8);
b = md5_HH(b, c, d, a, x[k + 2], S34, 0xC4AC5665);
a = md5_II(a, b, c, d, x[k + 0], S41, 0xF4292244);
d = md5_II(d, a, b, c, x[k + 7], S42, 0x432AFF97);
c = md5_II(c, d, a, b, x[k + 14], S43, 0xAB9423A7);
b = md5_II(b, c, d, a, x[k + 5], S44, 0xFC93A039);
a = md5_II(a, b, c, d, x[k + 12], S41, 0x655B59C3);
d = md5_II(d, a, b, c, x[k + 3], S42, 0x8F0CCC92);
c = md5_II(c, d, a, b, x[k + 10], S43, 0xFFEFF47D);
b = md5_II(b, c, d, a, x[k + 1], S44, 0x85845DD1);
a = md5_II(a, b, c, d, x[k + 8], S41, 0x6FA87E4F);
d = md5_II(d, a, b, c, x[k + 15], S42, 0xFE2CE6E0);
c = md5_II(c, d, a, b, x[k + 6], S43, 0xA3014314);
b = md5_II(b, c, d, a, x[k + 13], S44, 0x4E0811A1);
a = md5_II(a, b, c, d, x[k + 4], S41, 0xF7537E82);
d = md5_II(d, a, b, c, x[k + 11], S42, 0xBD3AF235);
c = md5_II(c, d, a, b, x[k + 2], S43, 0x2AD7D2BB);
b = md5_II(b, c, d, a, x[k + 9], S44, 0xEB86D391);
a = md5_AddUnsigned(a, AA);
b = md5_AddUnsigned(b, BB);
c = md5_AddUnsigned(c, CC);
d = md5_AddUnsigned(d, DD);
}
return (md5_WordToHex(a) + md5_WordToHex(b) + md5_WordToHex(c) + md5_WordToHex(d)).toLowerCase();
}